Google announced last month that in the upcoming version (version 85) of its popular browser it will warn users if the form they are trying to submit is insecure; but how is this defined?
The definition that Google is using, and indeed, a rather standard definition for this, is that any forms not submitted over the HTTPS (Hypertext Transfer Protocol Secure) Protocol are insecure.
Generally on the web, there are two main protocols that people use to access websites. These are:
- HTTP (Hypertext Transfer Protocol)
- HTTPS (Hypertext Transfer Protocol Secure)
The significant difference between these two protocols is that HTTPS is encrypted, whereas HTTP is not.
When something is encrypted, it doesn’t make it inherently safe; for example it is still possible for a website served via HTTPS to try and exploit security vulnerabilities to install malware on your machine, however, it does make it much harder for third parties to try and access your data in-transit.
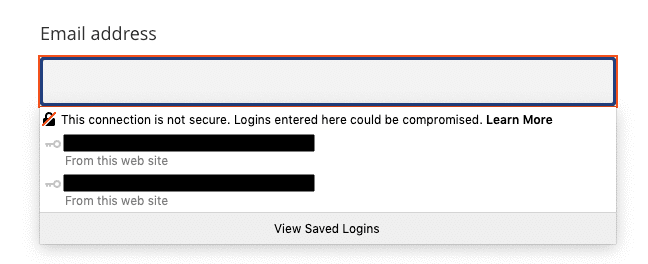
What this means is that if you submit a form over HTTP, if someone manages to intercept this submission when it is being sent from your computer to the website (server) in question, it is reasonably easy for them to decipher the information that you have submitted. If you have submitted sensitive information, for example you have entered your password to login to a service, this is not exactly ideal. This type of attack is generally referred to as a ‘man-in-the-middle attack’.
If the form is submitted over HTTPS, in simple terms this means that the form contents will be encrypted in a way that makes it very difficult (in some cases – impossible with current technology) for someone who intercepts the data to decipher the real contents of the traffic.
This is why Google is flagging this to users – they don’t want people to be at potential risk of their personal information being intercepted and used for nefarious purposes.
The history (and do other browsers do this?)
Historically speaking, most of the web used to run over HTTP. It is only in recent years that there has been real momentum to try and run the web via HTTPS by default. This is in large part due to increased awareness of security, and some high profile cases of secret surveillance programmes, which highlight the amount of information that can be obtained when accessing websites via the insecure HTTP protocol.
Over the last few years, there have been a number of high profile campaigns and changes to try and ensure more of the web is delivered using the HTTPS protocol. Good examples include the 2016 campaign by the Electronic Frontier Foundation (EFF) to encourage adoption, and the launch of services like Let’s Encrypt; which significantly reduces the barrier to entry for smaller businesses wanting to utilise HTTPS.
As part of this push, other browsers have also made similar changes to Chrome with regards to forms submitted via HTTP. Firefox, for example, implemented a similar warning in 2017.
Due in part to these campaigns and ventures, HTTPS is now the predominant protocol for serving content on the web. Telemetry data from Firefox shows that roughly 80% of all web pages loaded by Firefox users are now loaded via HTTPS – a figure that is likely to be similar across other browsers.
What should I do to ensure my website doesn’t show these warnings?
To ensure that these warnings don’t appear on your website, you need to ensure that your site is served via HTTPS, and not HTTP. It is also best practice to either redirect HTTP traffic to run on HTTPS, or better yet, utilise the HTTP Strict Transport Security (HSTS) security mechanism to ensure that your site can only ever be accessed via HTTPS.
There are many ways that you can obtain an SSL certificate these days. We often use Let’s Encrypt, as they offer a simple and free mechanism for obtaining an SSL certificate. Although implementing the certificate obviously requires additional changes to the hosting environment itself to ensure that traffic is sent properly via HTTPS (the certificate is really only a verification step).
To check if your website is running via HTTPS or not, all you need to do is visit the website in question, then select the padlock icon next to the URL in the URL bar of your chosen web browser:


This padlock will detail whether your site is running over HTTPS or not.
If your website is not running via HTTPS, then we would recommend contacting your hosting provider or developer as soon as possible to discuss remedying the situation.
In Conclusion
We ensure that all new websites we develop here at Studio 24 are delivered using the secure HTTPS protocol, and we would recommend anyone else running a website ensures their website is delivered using HTTPS as well to ensure their users are not susceptible to certain security vulnerabilities.
Thankfully due to increased awareness and campaigns over the last few years, ensuring your site runs via HTTPS has never been simpler or cheaper, and is often part of a standard package when paying for a website; whether that be with a development agency, or a website building platform like Squarespace or WordPress.com.
